I had the privilege of participating in the CSAW’23 Quals CTF as a member of InfosecIITR, and it proved to be a great experience. I am delighted to share the writeups for the reversing challenges my team and I successfully solved during the competition.
Reversing
Rebug1
Description:- Can’t seem to print out the flag :( Can you figure out how to get the flag with this binary?
Challenge File: file
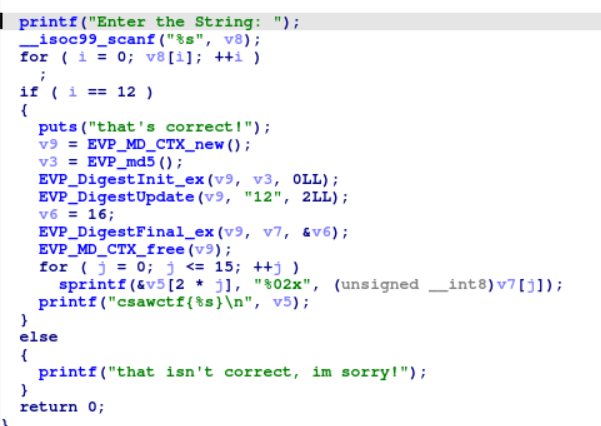
This challenge was beginner level reversing challenge. To see the decompiled code, open the provided binary in IDA and press F5.
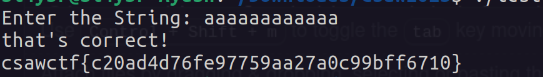
According to the code, the user is expected to input a 12-character string, and if the string length matches, they will receive a flag in response to the input. Now run the binary and give any 12-character input and you’ll get the flag.
Flag:- csawctf{c20ad4d76fe97759aa27a0c99bff6710}
Rebug2
Description:- No input this time ;) Try to get the flag from the binary. When you find the answer of the program, please submit the flag in the following format: csawctf{output}
Challenge File: file
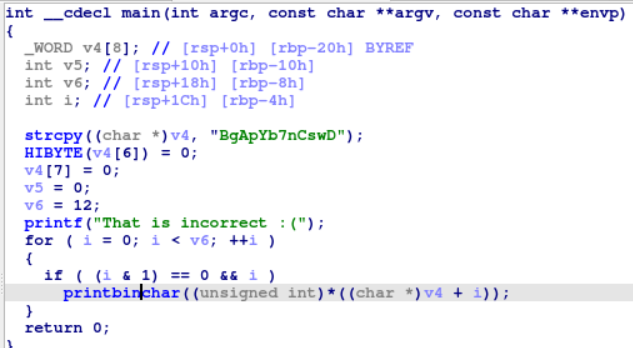
This time, there is no need of input as it was in Rebug1. So let’s have a look at the source code first. Open the binary in IDA and decompile it (pressing F5).
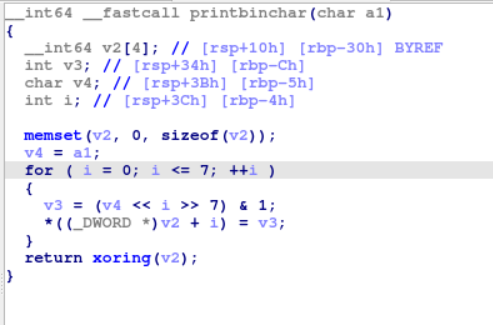
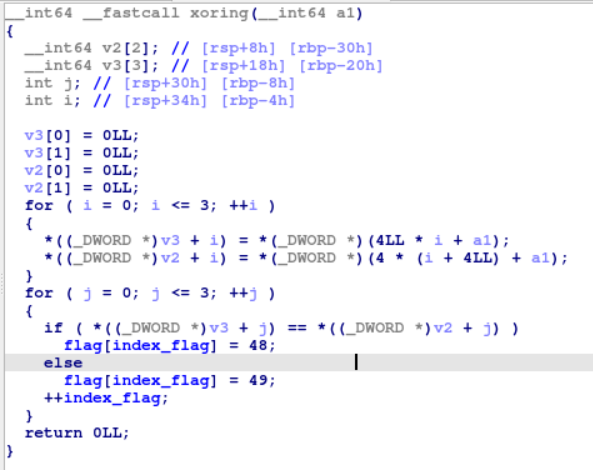
Initially, a string is provided to us which undergoes certain operations and then another function printbincharis called only when (i & 1) == 0 && i -this condition is satisfied (i should be even and non-zero). Now look at printbinchar function.
In this function, v4<<i>>7 a left shift operation is done which shifts its bits left by i positions and then right shift operation which shift its bits right by 7. The purpose of this function is to represent a char in in its binary form. But here again another function xoring is being called. Here, its pseudo-code :-
Now, we have almost reached to our final destination. If above conditions are met, then ‘0’ will be added to our flag and if not, then ‘1’. So, to get flag, I just copied the above pseudo-code and modified it. I added print(flag) and ran it. Here it is- file
Flag:- csawctf{01011100010001110000}
Impossibrawler
Description:- How do I beat these guys ?
This game was based on game-reversing. It was a nice challenge as it made me to spend a lot of time as I overlooked something very basic. So let’s discuss:-
First, I ran the .exe file and found the flag was only accessible after completing two levels, but main catch here was, the bullets which player was firing were not causing the damage to enemies and thus their health remained constant. So in short, game was unbeatable by human(atleast for me as I’m very bad at gaming) to get flag.
I first approached it by Cheat Engine to get control over required variables and I tried searching for strings too.. but it was not of any help. Then I tried to extract files from exe itself but it was also a futile effort. Then I thought about the game-engine used:- Godot Engine. I googled about godot engine game reversing and got this helpful tool- link. I used .pck file for unpacking my game and successfully recovered the project files.
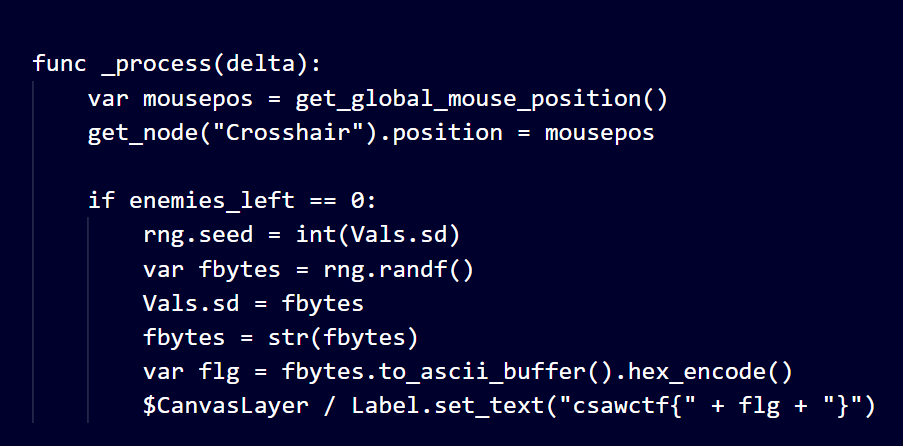
In level_2 script, when enemies_left == 0 range of a random number generator is seeded with the value obtained from int(Vals.sd) after which random floating number is generated, fbytes is converted to string. Flag is obtained by converting fbytes to ascii followed by hex encoding. Since Vals.sd is required, so I looked in level_1 script to check whether it was being updated. Yes, in level_1, Vals.sd was storing fbytes when enemies_left == 0. Initially vals.sd was set 0. The basic thing I overlooked the functionality of randf() which returns values between 0 and 1, so it does not matter whether vals.sd is updated or not because in level_2 it is casted into int type which makes it 0.
var rng = RandomNumberGenerator.new()
rng.seed = 0
var fbytes = rng.randf()
fbytes = str(fbytes)
print(fbytes)Output is 0.202272. For flag, convert this to ascii and then in hex, i.e., 302e323032323732. This is our flag. Flag:- csawctf{302e323032323732}
Misc
AndroidDropper
Description:- The app does nothing!
Challenge File: file
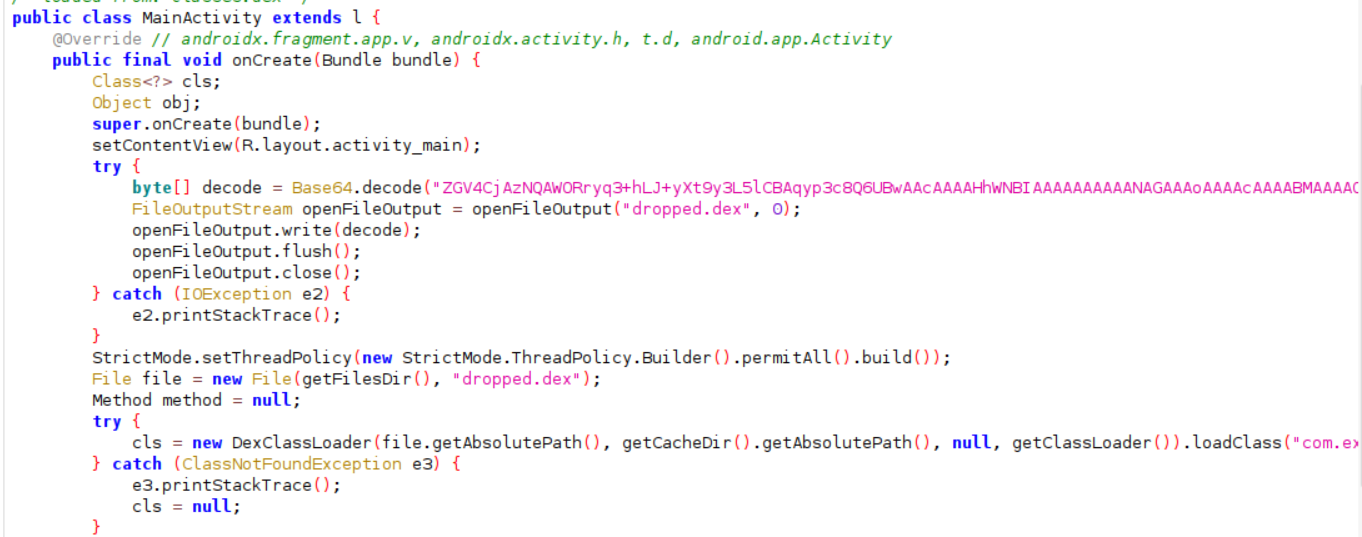
This was an easy android reversing based challenge. For android reversing, I use jadx tool to view the source code. In jadx, navigate to com.example.dropper and here the code is :-
Some base64 encoded data is given which is written to dropper.dex after being decoded. I did the same, decoded the data, got the .dex file content. Then to analyze the dex file, I ran jadx -d d_jadx dropper.dex command.
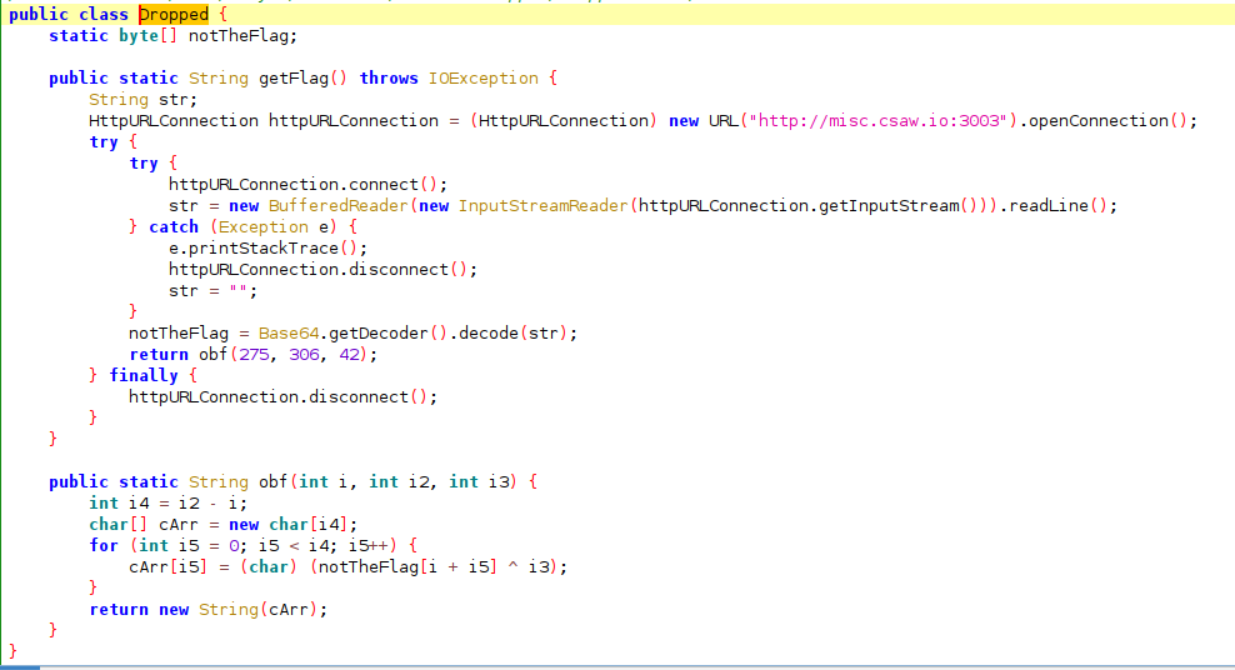
Now, there is a link given in code, clicking on it, gave base64 data. Decoding base64 data is stored in notTheFlag variable and obf function is now called. So, we got the flag, using decoded data, which is passed in obf.
Flag:- csawctf{dyn4m1c_lo4deRs_r_fuN!}