Hi again! In this blog, I have reversed a malware containing LummaC2 stealer.
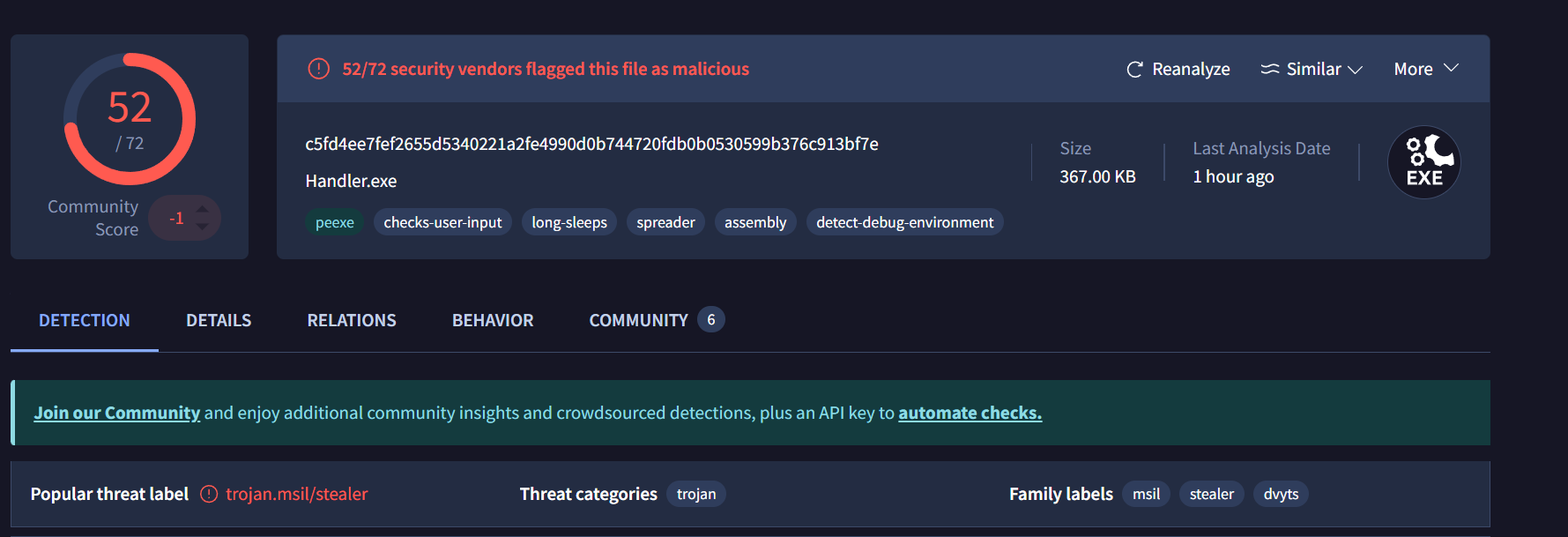
Basic Analysis
- SHA-256 of the file is:
c5fd4ee7fef2655d5340221a2fe4990d0b744720fdb0b0530599b376c913bf7e - The original name of the binary is
Handler.exeand it’s a.NET executable - Looking at the strings, lot of base64 encoded strings are present, it suggests there may be some kind of string obfuscation.
Static Analysis
For analysing the malware, I used
dnSpyas our malware is.NET executable.![image]()
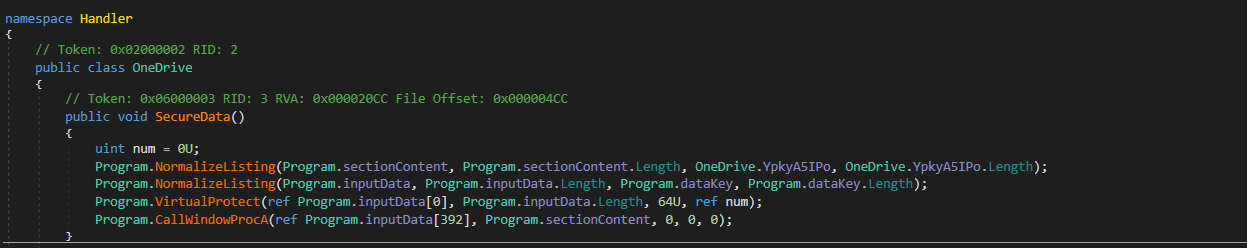
- WinAPIs like
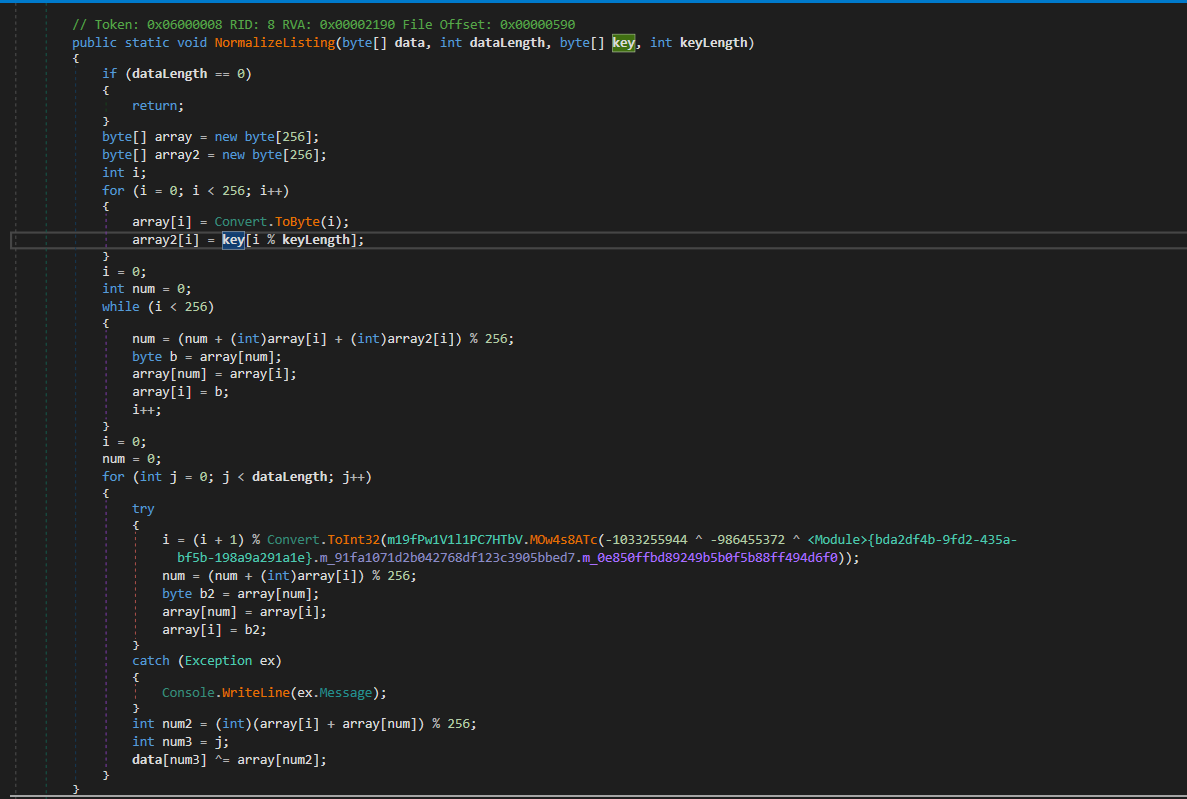
VirtualProtectandCallWindowProcAare present: it suggests the presence ofshellcode. So, it leverages theVirtualProtectcall to make the shellcode memory region executable and abuses theCallWindowProc APIto execute the shellcode. Program.VirtualProtect(ref Program.inputData[0], Program.inputData.Length, 64U, ref num);Taking references from Microsoft docs, third param isflNewProtect: memory protection option, and here64is being passed that isPAGE_EXECUTE_READWRITE. It confirmsinputDatais the shellcode.- This function implements RC4 encryption algorithm.
DataKeyis :{ 92, 102, 121, 128, 113, 104, 212, 200, 111, 37, 50, 69, 96, 76, 234, 96, 208, 253, 98, 100, 81, 137, 30, 48, 163, 184, 164, 191, 123, 212, 74, 195, 119, 36, 4, 61}-> The key for RC4 decryption of shellcode- Similarly,
inputData(or shellcode) and key for decryptingsectionContentare also hardcoded.![image]()
This above code is the part of the Main function. It extracts the binary path and then checks for MZ and PE headers for a valid PE file.
- There is a loop where a string is encoded as
base64and comapared. - From
Program.SectionContent, it seems program sections names like.text,.reloc,.rsrcand.idataare being compared and if the check passes, data is copied of that section. - It seems, this is a packed malware, which will be decrypted with RC4 and then executed.
- We can verify this using the debugger.
Dynamic Analysis
- Now, let’s try to analyse the behaviour of the malware.
- Run the binary in the sandboxed environment only, to avoid any undesirable consequences.
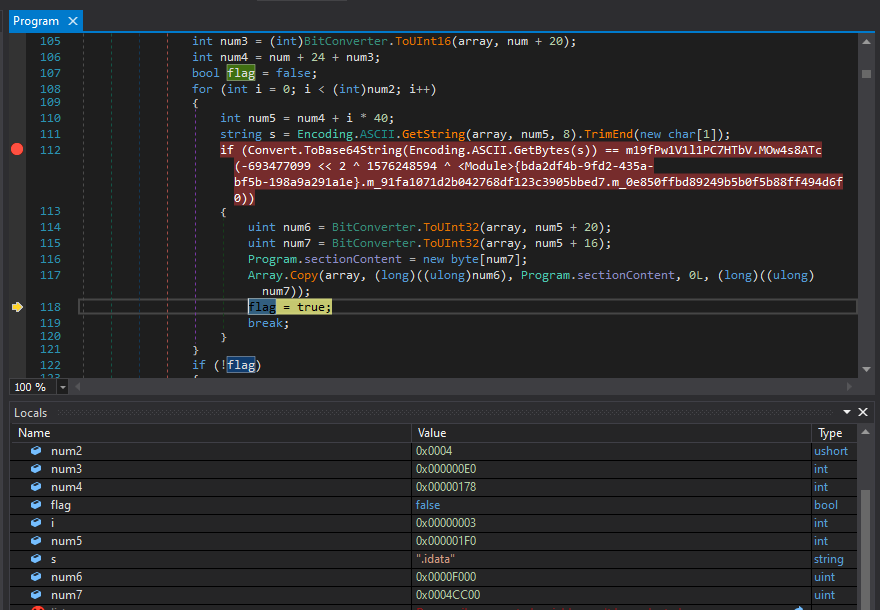
- So, first it checked for
s = ".idata"(base64 string wasLmlkYXRh) and then it copied the data from0xf000to0x5bbff(offsets of the binary), data length is0x4cc00![image]()
- Now, reversing
SecureData, in first call ofNormalizeListing,.idatadata is being passed along with the key (length:0xA) - Key is:- [0xA, 0xB, 0x1, 0x12, 0x0C, 0x57, 0x88, 0x0B, 0xFF, 0x0C]
- In second call of
NormalizeListing, nowinputData(shellcode) is being passed along with the key (length:0x24) [Key already mentioned in above block] Our both data are decrypted with RC4 now and another PE file (packed binary) comes out. Let’s try to analyse it.
- Running
flosson this PE file, gives some interesting results:
Content-Disposition: form-data; name="
Content-Type: attachment/x-object
Content-Disposition: form-data; name="file"; filename="
hwid
send_message
Eact
file
Content-Type: multipart/form-data; boundary=
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
\Last Version
%Program
pplication\
advapi32.dll
SeImpersonatePrivilege
winc
json
http://localhost:
\Local Extension Settings\
/Extensions/
key4.db
cert9.db
cookies.sqlite
logins.json
formhistory.sqlite
\key4.db
ole32.dll
LOCK
\Packages
Thunderb
\LocalState\Indexed\LiveComm\
.eml
Mails/Windows Mail
DiscordCanary
DiscordPTB
\Local State
os_crypt.encrypted_key
/dp.txt
Path:
Configuration:
Buy now: TG @lummanowork
Buy&Sell logs: @lummamarketplace_bot
LummaC2 Build: Jan 15 2025
LID:
%SystemDrive%
ROOT\CIMV2
SELECT * FROM Win32_BIOS
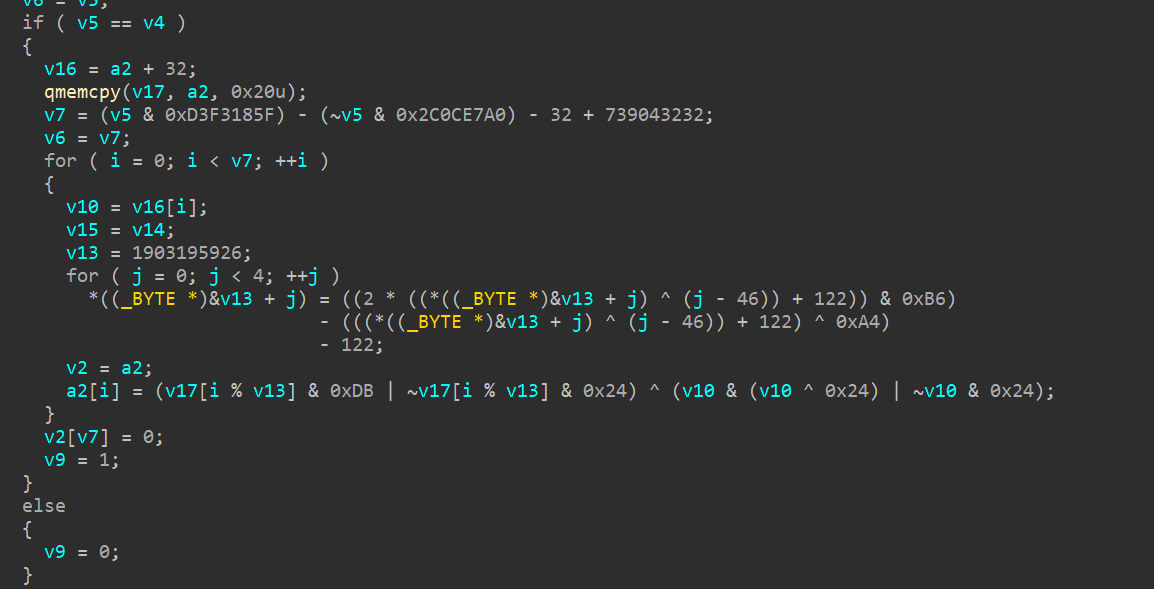
SerialNumberHere is the function which decrypts
base64strings (e.g.Bm1NE4MDSBkzp0zZyP6i4LdYDOjfYRjN+sZUfIYz8lxvACB872I8fFDPLbWkm8zO1TdijA==) to the domains:![image]()
Malicious Domains captured in
Wireshark:
crookedfoshe.bond
strivehelpeu.bond
immolatechallen.bond
growthselec.bond
jarry-deatile.bond
pain-temper.bond
stripedre-lot.bond
jarry-fixxer.bond
culltereddirtys.click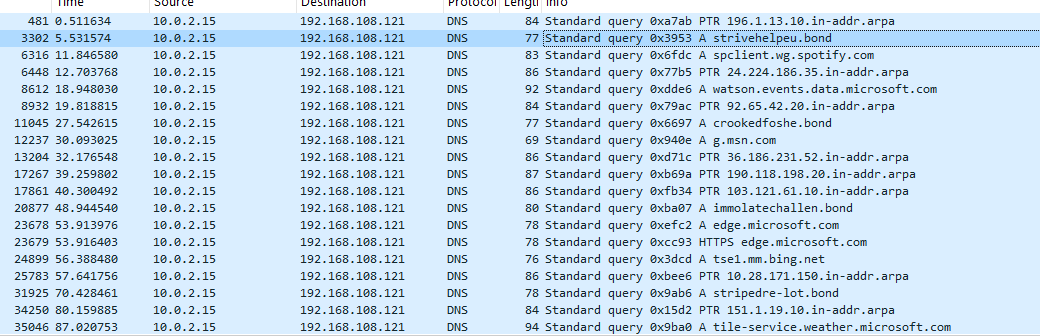
 Setting up and communicating with C2 Server
Setting up and communicating with C2 Server
- Malicious IP addr:
172.67.131.36104.21.3.197172.67.199.224
https://steamcommunity.com/profiles/76561199724331900 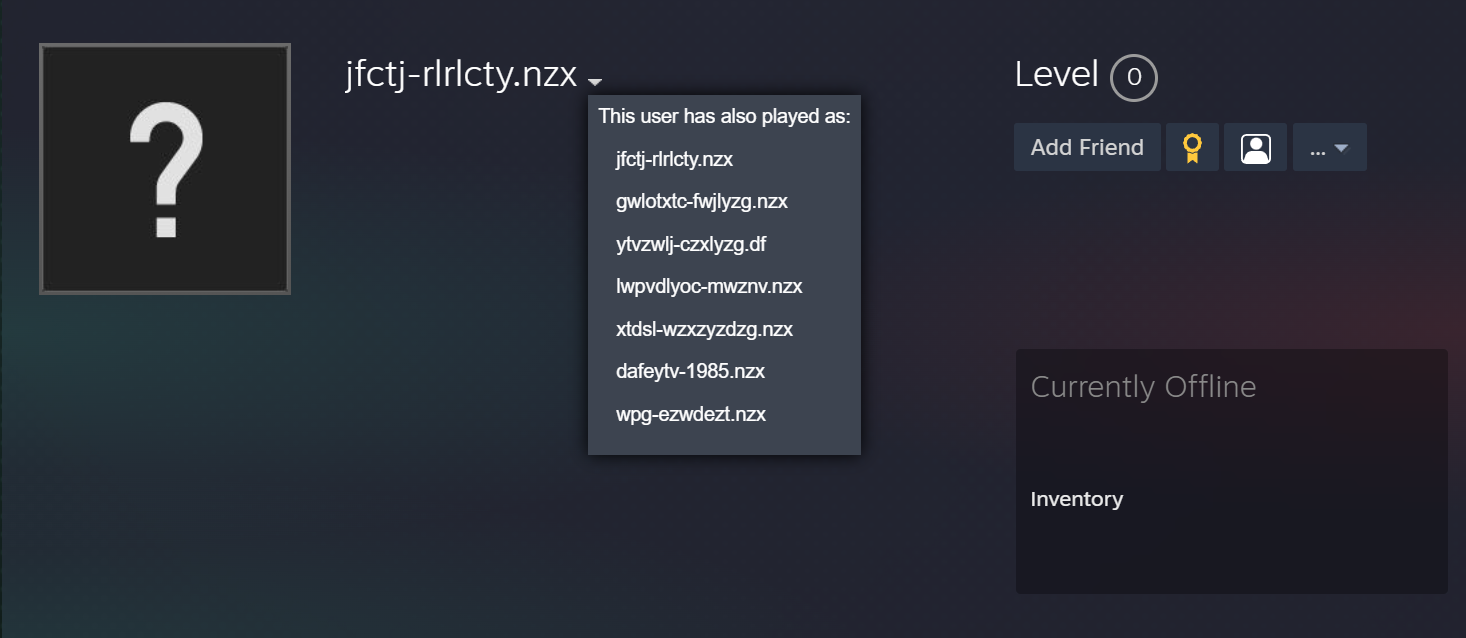
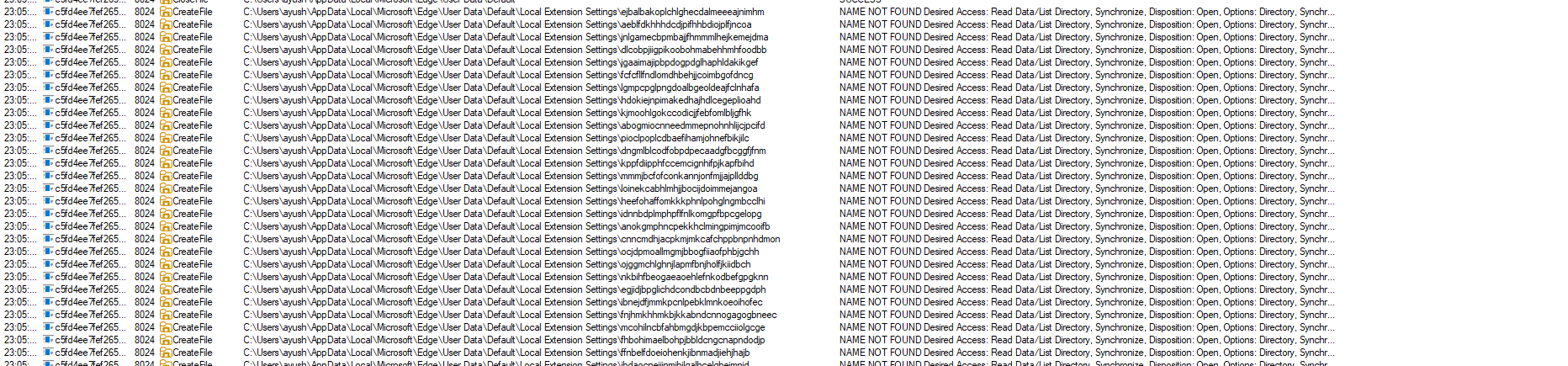
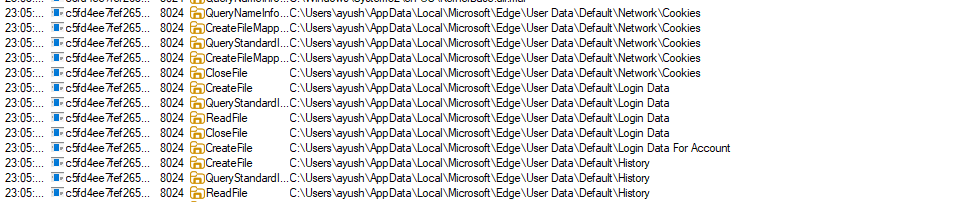 Collecting data of Edge Browser
Collecting data of Edge Browser
Conclusion
- Binary Packing
- Abusing
CallWindowsProcA()for shellcode execution. PEB traversal and API hashing- Setting up C2 server
- Using
DDR (Dead Drop Resolver)to hide its C2 details on the steam community website. - Contacting malicious domains
- Stealing sensitive files like:
key4.dblogins.jsoncert9.dbos_crypt.encrypted_keyand many more. - It targets Browsers, CryptoWallets, Extensions, Messaging Apps (like Telegram, Discord), Email Clients (like Thunderbird, PMAIL, The BAT!)
 Telegram channel associated with LummaC2.
Telegram channel associated with LummaC2.
References
- https://osandamalith.com/2021/04/01/executing-shellcode-via-callbacks/